Видео с ютуба Security Best Practices

Kubernetes Security Best Practices you need to know | THE Guide for securing your K8s cluster!

Security Role Management Best Practices

Лучшие практики безопасности — CompTIA A+ 220-1102 — 2.6

MCP security best practices

Password Security Best Practices

Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)

Cybersecurity Best Practices: Beyond the Basics

Top 4 Security Best Practices for Your Android App

React Security Best Practices: A Beginner's Guide to Secure Coding 🛡️
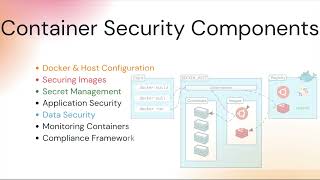
Top 10 Docker Container Security Best Practices with Tutorial

Security Best Practices For Building Data Applications With Snowflake

What Is an API? | API Security Explained | API Security Best Practices | Simplilearn

AWS Summit ANZ 2022 - Security best practices the well-architected way (SEC3)

5 DevOps Security Best Practices for your SaaS App

Top 5 cloud security best practices checklist | Cyber security awareness training |Security Quotient

Security Best Practices

Essential AWS Security Best Practices: Building Workloads the Well-Architected Way | AWS Events

Azure Security best practices | Azure Tips and Tricks

Protect Your Business 7 Security Best Practices for Microsoft 365